Hello friends today i give you information about SQL Injection & how to detect it. SQL Injection (SQLi) attacks have been around for over a decade. You might wonder why they are still so prevalent. The main reason is that they still work on quite a few web application targets. In fact, according to Veracode’s 2014 State of Security Software Report , SQL injection vulnerabilities still plague 32% of all web applications. One of the big reasons is the attractiveness of the target – the database typically contains the interesting and valuable data for the web application.
A SQLi attack involves inserting a malformed SQL query into an application via client-side input. The attack perverts the intentions of web programmers who write queries and provide input methods that can be exploited. There is a reason they’re on the OWASP Top 10. Termed “injection flaws”, they can strike not only SQL, but operating systems and LDAP can fall prey to SQLi. They involve sending untrusted data to the interpreter as a part of the query. The attack tricks the interpreter into executing commands or accessing data. Attackers use this exploit to modify entries in your database, execute commands on the database (delete databases, change permission and so on) and read and exfiltrate data from your databases.
Examples of SQLi attacks can be found on the OWASP wiki. The underlying flaws enabling SQLi attacks are introduced when developers create dynamic database queries that include user input.
Remediating SQLi attacks involves fixing coding defects that allow user-supplied input that can contain malicious SQL from modifying the logic of the query. The OWASP wiki details some suggested defenses that application developers use to avoid introducing SQLi-enabling flaws.
The first step in dealing with SQLi exploits is detecting and investigating them. When under attack, the following questions are critical:
- When was I attacked?
- Where was I attacked?
- How widespread was the attack?
- Were any files or tables overwritten?
- Who is attacking me, and are others being attacked as well?
Using AlienVault USM to Detect SQL Injection Attacks
AlienVault Unified Security Management (USM) can help you detect these attacks and answer the questions above with several integrated security technologies including host-based IDS, network IDS and real-time threat intelligence.
Network IDS spotting SQLi
AlienVault Unified Security Management (USM) can help you detect these attacks and answer the questions above with several integrated security technologies including host-based IDS, network IDS and real-time threat intelligence.
Network IDS spotting SQLi
The Network Intrusion Detection (NIDS) built-in to AlienVault USM gives you the ability to monitor all connection requests coming to your web server, plus it includes built-in correlation directives to spot activity indicative of a SQLi. Since the threat landscape is always changing, the Network IDS signatures are updated weekly based on threat research conducted by the AlienVault Lab research team, so you can stay current on new attacks.
Host IDS detecting SQLi by watching file activity
USM also includes a Host-based Intrusion Detection System (HIDS) so you can monitor activity locally on a server. In this case, the HIDS agent would be installed on the web server itself, parsing the logs on your Apache or IIS server. Again, the built-in correlation rules in AlienVault USM make it possible to detect activity consistent with SQLi attacks and alert you immediately. The AlienVault HIDS also monitors changes to files so you have visibility into which files and tables in your database were affected by the attack.
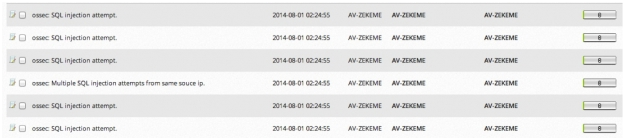
Here’s an example of the USM console displaying SQLi and the associated threat details:
HIDS Dashboard
List of Recent SQLi Events
Details about the Threat
Real-time Threat Intelligence from the AlienVault Open Threat Exchange
In addition, AlienVault USM uses real-time threat intelligence from the AlienVault Open Threat Exchange (OTX) to spot connections with known bad actors. These are known malicious hosts or attackers whose IPs have shown up in OTX because they attacked other OTX contributors, have been identified by other threat sharing services we use, or have been identified via independent research conducted by our AlienVault Labs team.
In addition, AlienVault USM uses real-time threat intelligence from the AlienVault Open Threat Exchange (OTX) to spot connections with known bad actors. These are known malicious hosts or attackers whose IPs have shown up in OTX because they attacked other OTX contributors, have been identified by other threat sharing services we use, or have been identified via independent research conducted by our AlienVault Labs team.
OTX data provides context to the IDS information and can increase your confidence that a threat detected is malicious, since the activity you are observing is from a known malicious host. In addition, USM combines and correlates input from HIDS, NIDS and OTX via its built-in Security Information and Event Management (SIEM) capabilities, giving you the full picture of threats in your environment.
Thanks for visit my blog....!!
By:- Hacker Squadron(Team)
[Dutch] Hallo vrienden vandaag geef ik u informatie over SQL-injectie en hoe om het te ontdekken. SQL Injection (SQLi) aanslagen zijn er al meer dan een decennium. Je kunt je afvragen waarom ze nog steeds zo gangbaar. De belangrijkste reden is dat ze werken nog steeds op een flink aantal webapplicatie doelen. In feite, volgens Veracode's 2014 State of Security Software Report, SQL injection kwetsbaarheden nog steeds teisteren 32% van alle webapplicaties. Een van de grote redenen is de aantrekkelijkheid van het doel - de database bevat meestal de interessante en waardevolle gegevens voor de webapplicatie.
[French] Bonjour les amis, aujourd'hui je vous donnent des informations sur l'injection SQL et comment le détecter. Injection SQL (SQLi) attaques ont été autour depuis plus d'une décennie. Vous pourriez vous demander pourquoi ils sont encore si répandue. La raison principale est qu'ils continuent à travailler sur un bon nombre de cibles d'applications Web. En fait, selon l'État de 2014 VeraCode du rapport des logiciels de sécurité, les vulnérabilités d'injection SQL gangrènent encore 32% de toutes les applications Web. Une des grandes raisons est l'attractivité de la cible - la base de données contient généralement des données intéressantes et précieuses pour l'application Web.
[Russian] Здравствуйте, друзья сегодня я даю вам информацию о SQL Injection & как обнаружить его. SQL Injection (SQLI) атаки были вокруг в течение более десяти лет. Вы можете спросить, почему они до сих пор так распространена. Основной причиной является то, что они все еще работают на довольно многих целей веб-приложений. На самом деле, в соответствии с Veracode в 2014 государства Security Software отчет, уязвимости SQL-инъекции еще чума 32% всех веб-приложений. Одна из главных причин является привлекательность цели - база данных, как правило, содержит интересные и ценные данные для веб-приложения.





![EA Sports UFC Serial Key Generator [PC, XBox, PS4] 2014](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj55wC5uDmE3rMFm8YWQK0-f1z3Osqi44-8l02G_yUm-xGqDjBTUmpCpKr4uWz6DNXOwqWT051kZ4tRIBtNPZZDte24Ac_fQWKCyEgg2ffor-zJKO-12JOmQU81XsgxtqVKf_nPat1mWYV2/s72-c/blgr.jpg)


![Sniper Elite 3 CD Key Generator [PC , Xbox , PS3]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgn0Wxjg6Labyuw2hZSU0e9gNM1dipnM4Cspk4VDMQQQIOtXIdolvm4SW6qCi5AfQZj7aEtDBppq_euzAG6tjzZTUz4wtNdaZWc7YM5_rx_dGPbCAjrUB0Lxp6eRnH5_a1lI0HAT5bRz-qq/s72-c/Sniper-Elite-III.jpg)







0 comments:
Thanks for Join us....!!!